What is Open Redirect vulnerability?
Open redirect vulnerabilities allow the attacker to use a well known website name to redirect the visitor to another website.
As mentioned in Everything is vulnerable ( Q4 in internet wars ). You should pay attention to URLs you visit by inspecting the form of the address carefully to make sure the address represents the website you are visiting.
However, Open redirect vulnerability is a development fault, As it allows the attacker to easily use the system to redirect users to another website without giving the user any clues about being redirected. So, a visitor visiting a maliciously crafted URL, yet still on the legit entity server, to find himself/herself on a totally different website.
About the vulnerability
Url : https://deploy.apple.com/qforms/open/register/country/avs
The “GET” parameters : action = & country= & returnUrl= .
For example: This link would redirect to TiTrias.com.
https://deploy.apple.com/qforms/open/register/country/avs?action=ab&country=ae&returnUrl=http%3A%2F%2Ftitrias.com%2F
Video ( POC )
Timeline
Apple took nearly 3 months and 10 emails to solve this vulnerability which is very long time to solve a simple vulnerability
– 13 / 2 / 2015 : Reporting the vulnerability.
– 11 / 5 / 2015 : Vulnerability Resolved.
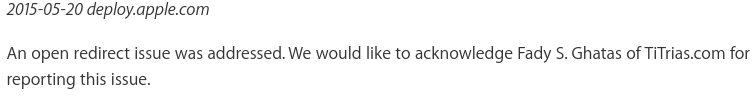
– 26 / 6 / 2015 : Acknowledgement published:
2015-05-20 deploy.apple.com
An open redirect issue was addressed. We would like to acknowledge Fady S. Ghatas of TiTrias.com for reporting this issue.












0 Comments