TiTrias Blog
Stay up to date with our new postsWhy Typescript? Is typescript frontend or backend?
TypeScript is a programming language that was developed and maintained by Microsoft. It is a superset of JavaScript, meaning that any valid JavaScript code is also valid TypeScript code. One of the main goals of TypeScript is to add type checking and other features to...
8 Lessons Twitter should learn from Windows Vista: Your organization structure decisions might become the root cause of your software low quality
TL;DR: Jump to our non-statistical summary! We often struggle with bugs, bad practices, non modular architecture. In previous posts, we keep mentioning Conway's law to show the correlation between system design and company communication channels: Any organization that...
Bless: Open-source Map-powered Simple Homeless Management Information System (HMIS)
Bless System allows you to automate and manage food distribution to homeless people, by creating groups consisting of group admins (One or more) and food servers (Those who prepare food and deliver it to homeless). On the system, you can store locations on map to...
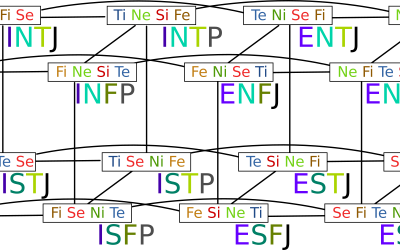
Product owners and Psychological types (Cognitive functions/MBTI)
Before starting, we want to lay-out some ground rules for this post, MBTI isn't a scientific theory, it's just a business indicator (Created by a writer not a psychologist), most of its tests aren't accurate, however, the indicator is built around "Jungian cognitive...
5 Free NGO systems in 2023
TiTrias 10th birthday is approaching fast, Although the company wasn't registered until March 2016, but the blog started way back in June 2013. We are giving the same opportunity to NGOs to have a complete solution! We will handle all technical work for the first year...
Nexus multi-scrum teams mono-repo trunk-based release management and misconceptions.
Note: This post is highly opinionated based on our experience in multiple Nexus projects A lot of teams struggle with releases! The argument is "the more complex the project gets, the more complex the releases are". Once you have this symptom, there is most certainly...
Why every tech startup needs to understand Nexus, portfolio management, monorepos and trunk-based development.
Any startup comes to the point where the first investment has been secured and a scaling plan should be structured, scaling here covers every aspect of it, from team and resources to processes and releases. All tech companies start deep thinking of the best ways to do...
8 areas of Typescript: VR, IaC, Extensions, Robots, Games, WebAssembly, runners and cross-platform.
We are actively using typescript for most of our development work nowadays. Earlier this year, we decided to use Typescript as our go-to language for backend. So NestJs on backend, and mostly Angular is our frontend champ. But that's not all, we are using Typescript...
16 Reasons why Typescript is becoming our backend go to language, but there is a lot to consider.
6 years ago, when we tried NodeJS for a large-scale project in TiTrias for the first time. We were not sold yet. And we continued suggesting Laravel as the go to backend stack, unless something requires Java or .NET stack. And as always, Angular for frontend. Since...
To do and NOT to do under DDoS
DDoS (Distributed Denial of Service) is a type of attacks to interrupt the continuous healthy response of a server, it's considered one of the hardest attacks to mitigate and has harvested so many sites. To understand how deep, bad and well hidden this type of attacks...
Applying Scrum to Content Creation Project: Reasons and Concerns
We love Scrum and Agile; Scrum gives any startup the easiest path to a working product with the least complexity. Our current product is a bit different, as the majority of activities aren't related to programming. The majority of the project is content writing and...
GANKIN: generating Kin faces using disentangled GAN (More Samples)
Paper: GANKIN: generating Kin faces using disentangled GAN Read more about the paper here Kin Generation using GAN - Video: https://www.youtube.com/watch?v=RV3EzxufA6c Samples with variable gender and age attributes Top row (Left: real fater, center: real...