Q1. Why was this post written ?
This post is highly recommended for all web surfers regardless of their interests; from online shoppers to social networks users.
Millions of defrauding are attempted every day and actually many succeed!
As a matter of fact, if you have social media accounts, you are one of two categories : Either your account is hacked or will be.
This post will talk about internet wars and how safe you are in the middle of this mess !
Note : Online systems means websites, online chatting applications, remote streaming, etc.
Q2. What are the main types of attacks ?
There are many many types of attacks that target online systems or users, Like social spamming, SQL injection, Cross-Site Scripting ( XSS ), OS commanding, etc…
However, Just for the sake of simplicity we can combine these into two main categories :
System targeted attacks.
This kind of attacks aims to hack into the system itself either to fetch sensitive data like users passwords and credit card numbers or to destroy the system.
This type of attacks targets the system as a whole not a certain group of users but requires that the system contains holes and vulnerabilities.
Example : The well-known heart bleed vulnerability which exposed sensitive data on most famous websites, Like : Facebook, eBay, Yahoo, etc.
(Any HTTPS website/system with a certain version of SSL library was a potential victim )
User targeted attacks.
This kind of attacks targets a single user or a group of users to gain access to their personal data.
For example a malicious phishing scam that has the same design of a popular website and purporting to be that popular trustful website; Once you enter your data ( Credit Card, Password, etc. ) your personal details are forwarded to the attacker.
A more popular examples are the social spamming techniques which allow a link to be spread without the permission of the victim.
This kind of attacks is less dangerous than the other type and actually depends on the user knowledge not the system weakness to success so we will concentrate on illustrating attacks that target the whole system and will give the ordinary users a 5-tip guide to avoid user targeted attacks.
Q3. What are the top 5 most dangerous types of hacks that targets online systems e.g. Websites( For System administrators) ?
-
OS Commanding.
OS Commanding ( A.K.A. Remote Shell Commanding ) is by far the most dangerous vulnerability. Imagine that you have a direct access to the system terminal ( in *NIX) or command line ( in Windows ).
Imagine you can directly send a command like rm * to a system which deletes all the files on the targeted system !!
-
Remote code execution ( RCE )
Remote code execution is very similar to OS Commanding but instead of executing a shell command, A programming language script is executed,
-
SQL Injection
SQL Injection allows the attacker to retrieve, edit or delete all data in the system’s database.
-
Admin panel bypassing
This vulnerability allows the attacker to bypass a secured panel either by bruteforcely trying combinations of data or by any other way
-
Cross-Site scripting ( XSS )
Similar to ( #2 Remote code execution) but instead of executing a script on the server side, A script is executed on the client side e.g. steal the victims cookie file.
Although, XSS doesn’t affect the system but is a system weakness as the system developer should disallow any kind of code injection.
[blockquote indent=”yes” ]
Injection is any kind of manually inserting custom code into the system to be executed, So the term injection is used to describe Vulnerabilities like OS Commanding, Remote Code Execution, SQL Injection, Cross Site Scripting.
[/blockquote]
Q4. Am I Safe in the middle of this mess? ( 5 tips User Guide )
Actually, Yes, And No, You will never be 100% safe but you can be safe enough to avoid severe types of attacks.
1- You should gain more knowledge about security to avoid becoming a victim of phishing websites and social spammers.
2- Always update your web-browser and use one of the well-known and secured browsers like Chrome, FireFox, etc..
3- Double check URL. Make Sure that the URL is directing to the website that you are visiting
[tabby title=”QUIZ”]
URL :
ABC://microsoft.com:apple.com@CNN.com.titrias.com/facebook.com
would direct you to :
1 – Microsoft.com
2 – Apple.com
3 – TiTrias.com
4 – Facebook.com
5 – ABC.com
6 – CNN.com
[tabby title=”Answer”]
The answer is : [highlight style=”yellow” ]TiTrias.com[/highlight]
The website name ( Domain name ) lays before the first slash ‘ / ‘ and contains digits, characters, dashes and dots only.
The URL
ABC://microsoft.com:apple.com@CNN.com.titrias.com/facebook.com/
is actually in a correct form; As:
– abc:// is the protocol ( Just like HTTP:// )
– Microsoft.com is the user name of the protocol
– Apple.com is the password of the user name of the protocol
– cnn.com is a sub domain in the domain name TiTrias.com
– TiTrias.com is the domain name
– Facebook.com is a relative path in the root of the subdomain of ( cnn.com.titrias.com )
So It’s like saying :
Access ( TiTrias.com ) domain through ( ABC ) protocol using username ( Microsoft.com ) and password ( Apple.com ) and then change direcotory to ( Facebook.com )
[tabbyending]
4- Don’t click any kind malicious links that are sent on your email or facebook account that you don’t guarantee it’s source !
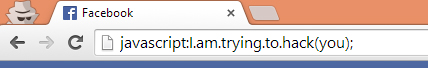
5- Don’t EVER copy and paste any kind of strings or URLs to your browser bar if you don’t know what you are doing ! Because url’s like
Javascript:blah(blah)
which is actually a script is more than enough to steal your account !
Everything is vulnerable ( Part Zero) : Introduction
Everything is vulnerable ( Part Two) : Internet wars
Everything is vulnerable ( Part Three) : “Windows” with no fences
Everything is vulnerable ( Part Four ) : Linux is vulnerable as well!












Thanks for sharing your info. I truly appreciate your efforts and I will be waiting for your next write ups thank you once again.
Thanks very interesting blog!