Vulnerability details.
Vulnerability detection.
AT&T are using Apache Solr for ajax searching in help files querying. Apache solr is immune to XSS, SQL injection & remote code execution. However, After following paths of solr ( Config, Schemas, etc ) I’ve finally found one panel ( videoservlet/admin ) left open with no restrictions.
Vulnerability Threats.
Solr admin panel exposes CWD of linux and user name. It gives access to configuration files and schemas as well.
Examples :
admin/stats.jsp
admin/get-properties.jsp
admin/schema.xml
The most dangerous threat is that Solr admin panel allows remote java code execution attacks using a remote XSLT response writer and allows adding new records or deleting and editing existing one.
Examples :
/update?stream.body=
stream.body accepts any query in xml form for example <update>…</update> or <delete></delete> and finally <commit></commit> for committing updates to the database.
That successful attack wouldn’t be possible if one doesn’t know Solr paths; That’s why web developers & whitehats should be familiar with all frameworks. At least framework paths and important files & directories.
Bug reporting procedure.
Firstly, If you aren’t registered to AT&T bug bounty program, you should !
Secondly, Report your vulnerability using AT&T bug bounty program form . You will get an automatic response in no more than 1 business day, If your submission has errors it will be rejected and you will be asked to resend your submission after eliminating causes of rejection.
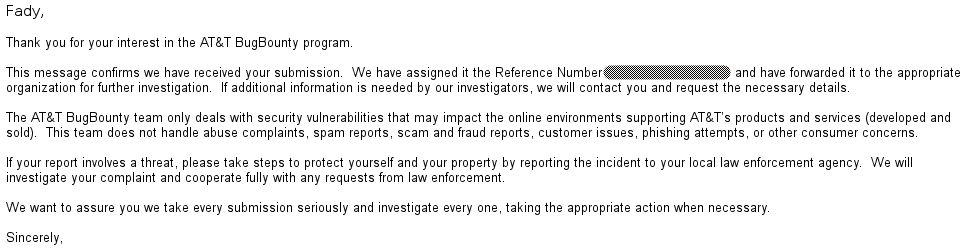
Then after almost 21 days AT&T have temporarily closed the admin panel so I sent them an email to ask for updates. The response was : 
Nothing about the reward so far. But I am honored & glad to be mentioned on AT&T hall of fame list. Thank you AT&T.
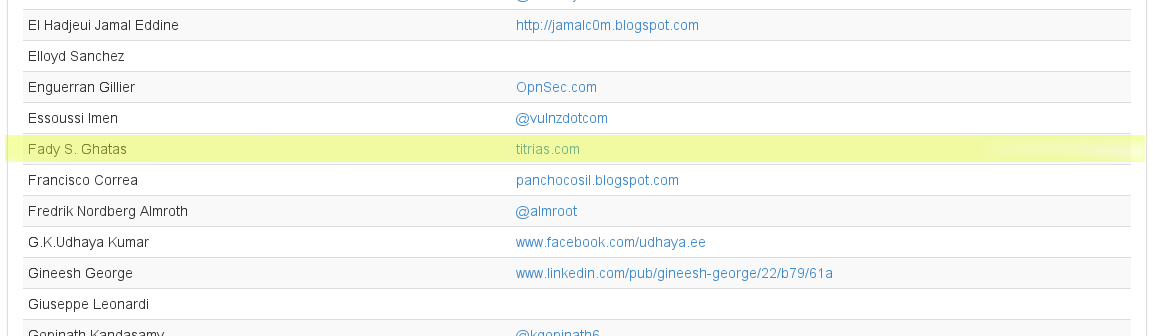
Next target will be Adobe. Did they left some panels open ?
Stay tuned.












0 Comments