TiTrias Blog
Stay up to date with our new postsConverting conditional GAN to unconditional GAN
Let me tell you something you already know. GAN ain't all sunshine and rainbows. Today, "GANKIN: generating Kin faces using disentangled GAN" is published in Springer, the article takes a different approach towards solving a complex generating problem: Generating Kins...
You got “email hacked” message? Here is what you need to do
Almost Daily, we get mails from our readers reporting that their mails got hacked. After getting a copy of these mails, we found out that all mails contain the same message but in different wording and in different language. In English, Korean or Japanese. I am sure...
SQL Joins – Part 2: Performance Tips and Tricks & Benchmark
This is the second article from SQL Joins series, you can find the first article here. It talks about the basic concepts of joins and compares between different types of inner and outer joins. If you aren't familiar with SQL Joins, kindly, read it first. Now, we are...
SQL Joins – Part 1: Difference between Inner Join and Outer Join
The concept of SQL joins is a must-have skill. Every developer should be able to use it in different use-cases with the best performance possible. This tutorial reveal the difference between Inner Join and Outer Join (Left Outer Join and Right Outer Join) in practical...
Reverse Engineering MBTI Tests
MBTI is one of the most well known methods used in recruitment process. HR departments in a lot of businesses relies heavily on the results of MBTI tests; however, the problem starts to come into focus when the results don't reflect the correct outcome , or at least...
Step-by-step to a USABLE KDE Archlinux Installation (Updated 2022)
UPDATE 2018: pacaur is no longer maintained, one of the best alternatives is trizen, the post is updated accordingly. UPDATE 2019: pacaur is back in business, still my favorite AUR helper tool Archlinux is still, by far, our best linux distro of all times....
Reset WordPress password using FTP only
Sometimes, you get yourself locked outside wordpress without any way to reset your password using email and you don't have database access. So here is the simplest way to reset your password without database access, only FTP is required. Create new file inside you...
Important commands to rescue hacked servers.
This post will you a boost in tracing the trails of your server intruder. You can use this post as a reference for your periodic server health checks as well. This is a very important article for server security specialists, white hats and developer in general....
Abandoning CouchDB (NoSQL) in favor of SQL
In short, Use CouchDB if you are 100% sure you won't need any (complex) joins. This post won't go through any theoretical differences or benchmark scores, only different use cases that I find really important to consider before using CouchDB. CouchDB is the dream DBMS...
Linux Best Code (Text) Editor : Atom, Sublime or Visual Studio Code?
Sublime Text I used ST2 in the past. How it works: Getting the job done as simple as possible. ST2 is pretty fast in starting up and in usage in general. Pros : Free for evaluation. Fast load up. Cons : Sublime Text can't be used commercially unless you buy a...
[How To] PouchDB and CouchDB : Database Per User Made Simple
CouchDB is one of the most powerful DBMS nowadays. However, although its documentation is good, there is not enough topics of how-tos and best practices for common use cases. One of these use cases is the database_per_user. Each user has his own private data that only...
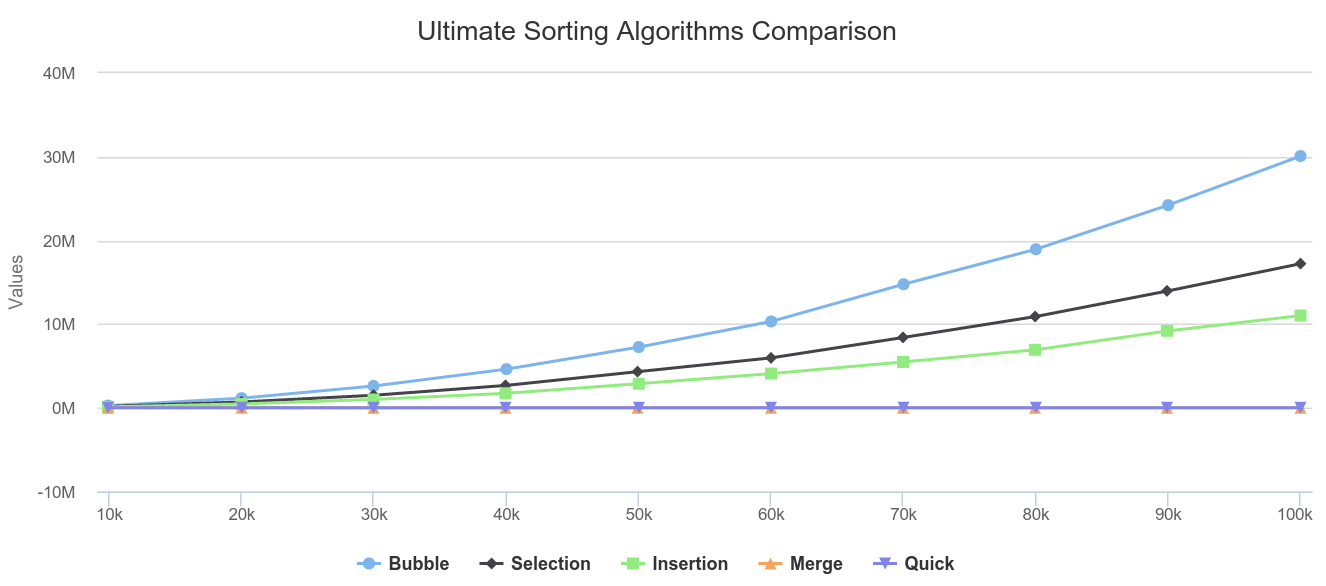
Ultimate Sorting Algorithms Comparison
Before the stats, You must already know what is Merge sort, Selection Sort, Insertion Sort, Bubble Sort, Quick Sort, Arrays, how to get current time. What is Stable Sorting ? A sorting algorithm is said to be stable if and only if two records R and S with the...