Sometimes, you get yourself locked outside wordpress without any way to reset your password using email and you don't have database...
Fady S. Ghatas Articles
Important commands to rescue hacked servers.
This post will you a boost in tracing the trails of your server intruder. You can use this post as a reference for your periodic server...
Abandoning CouchDB (NoSQL) in favor of SQL
In short, Use CouchDB if you are 100% sure you won't need any (complex) joins. This post won't go through any theoretical differences or...
Linux Best Code (Text) Editor : Atom, Sublime or Visual Studio Code?
Sublime Text I used ST2 in the past. How it works: Getting the job done as simple as possible. ST2 is pretty fast in starting up...
[How To] PouchDB and CouchDB : Database Per User Made Simple
CouchDB is one of the most powerful DBMS nowadays. However, although its documentation is good, there is not enough topics of how-tos and...
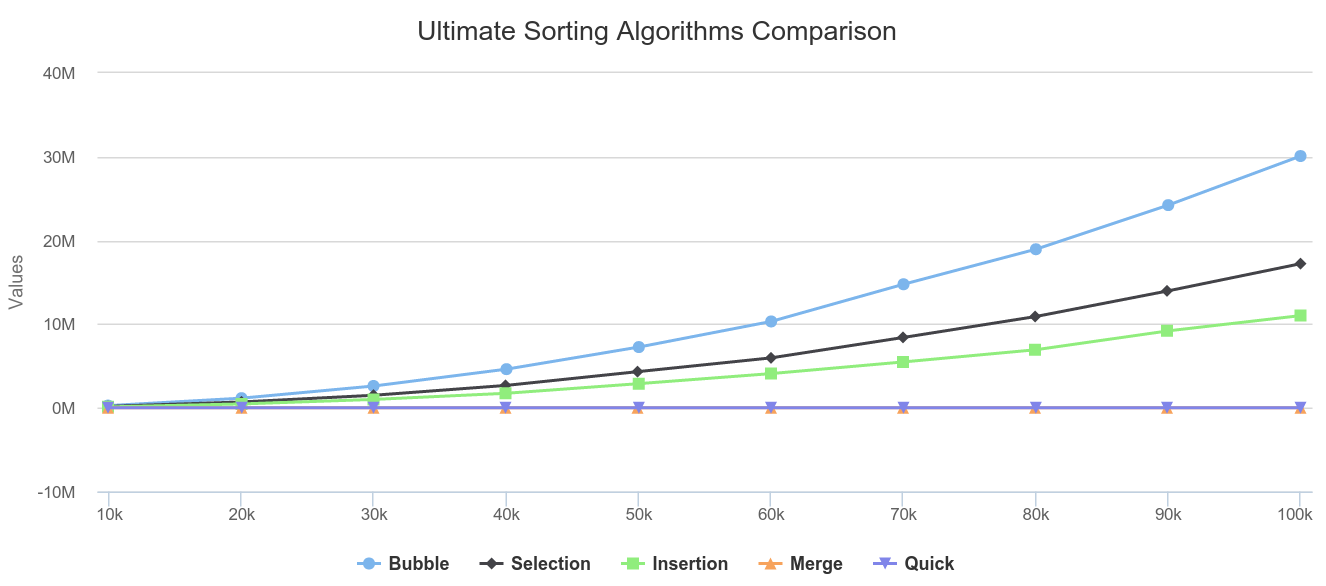
Ultimate Sorting Algorithms Comparison
Before the stats, You must already know what is Merge sort, Selection Sort, Insertion Sort, Bubble Sort, Quick Sort, Arrays, how to get...
White Hat Hacking : Apple open redirect vulnerability
What is Open Redirect vulnerability? Open redirect vulnerabilities allow the attacker to use a well known website name to redirect the...
White Hat Hacking – RedHat Cross Site Scripting ( XSS )
White Hat Hacking - Redhat cross site scripting ( XSS ) Using an ordinary Cross site scripting payload, The vulnerability could NOT be...
Everything is vulnerable II : Internet wars
Q1. Why was this post written ? This post is highly recommended for all web surfers regardless of their interests; from online shoppers to...